November 2018
Intermediate to advanced
382 pages
11h 20m
English
Ideally, misuse cases will be created during the upfront threat modeling process. Many specific misuse patterns can then be generated for each misuse case. Misuse patterns should be low-level enough that they can be decomposed into signature sets applicable to the monitoring technology (for example, IDS/IPS, SIEM, and so on) that will be used both on-premises and in your cloud environment.
Patterns can include device patterns, network patterns, service performance, and just about anything that indicates potential misuse, malfunction, or outright compromise, as follows:
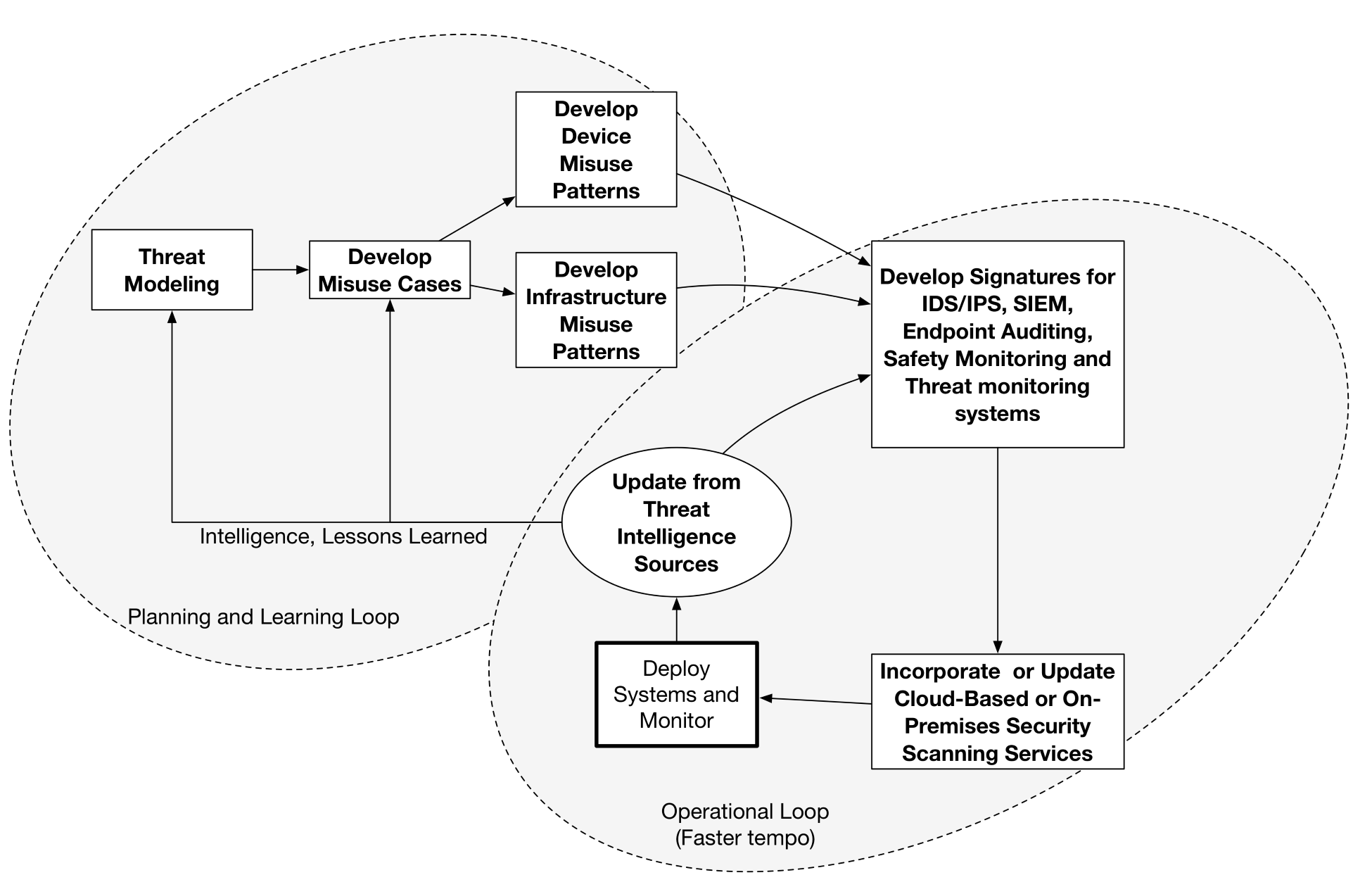
In many IoT use cases, SIEMs can be ...