November 2018
Intermediate to advanced
382 pages
11h 20m
English
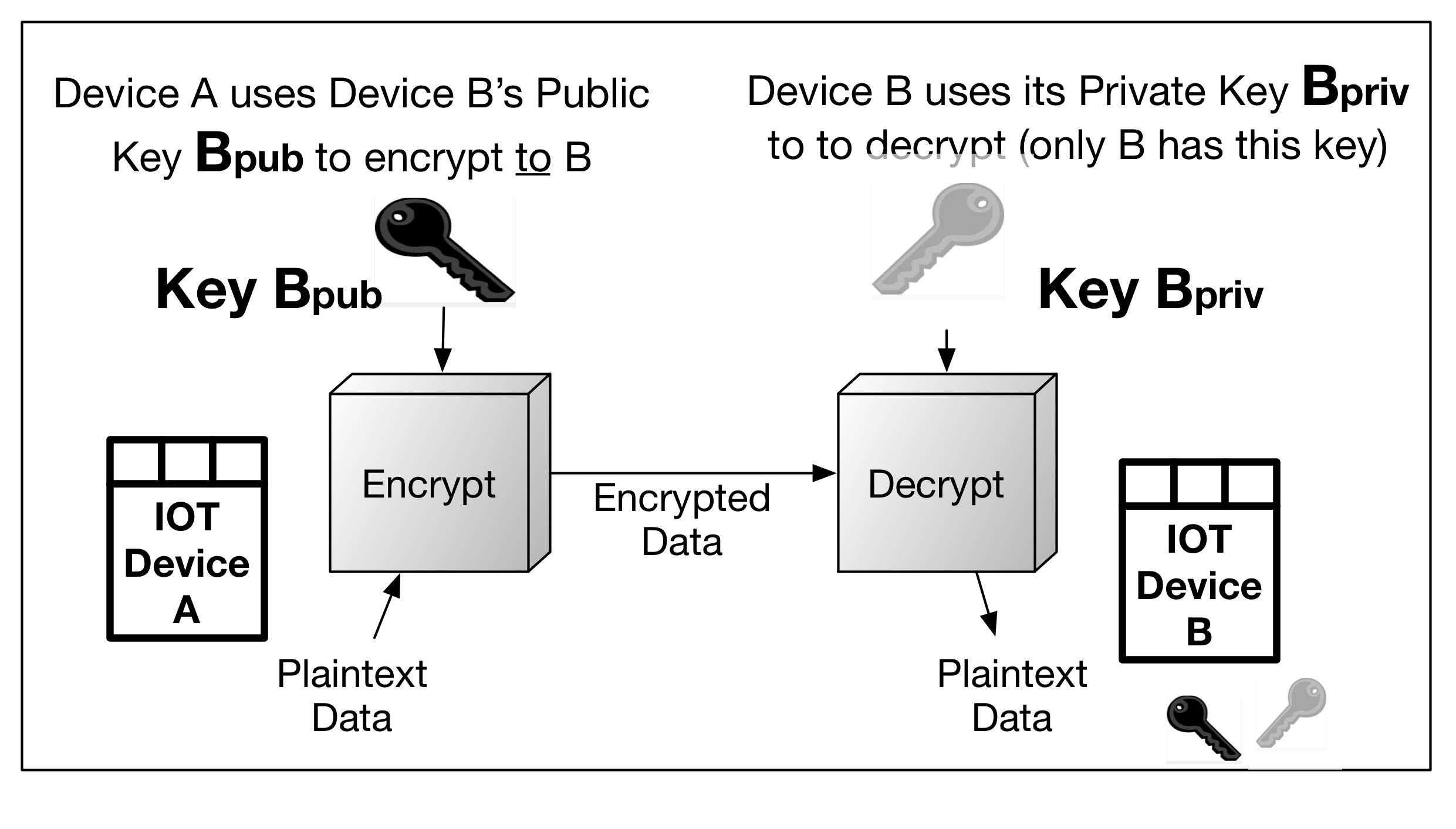
Asymmetric encryption simply means there are two different pairwise keys, one public and the other private, used to encrypt and decrypt, respectively. In the following diagram, IoT device A uses IoT device B's public key to encrypt to device B. Conversely, device B uses device A's public key to encrypt information to device A. Each device's private keys are kept secret; otherwise, anyone or anything possessing them will be able to decrypt and view the information:
The only asymmetric encryption algorithm in use today is that of Rivest, Shamir, Adelman (RSA), an Integer Factorization Cryptography ...