HTTP: The Definitive Guide
by David Gourley, Brian Totty, Marjorie Sayer, Anshu Aggarwal, Sailu Reddy
Public-Key Cryptography
Instead of a single encoding/decoding key for every pair of hosts, public-key cryptography uses two asymmetric keys: one for encoding messages for a host, and another for decoding the host’s messages. The encoding key is publicly known to the world (thus the name public-key cryptography), but only the host knows the private decoding key (see Figure 14-8). This makes key establishment much easier, because everyone can find the public key for a particular host. But the decoding key is kept secret, so only the recipient can decode messages sent to it.
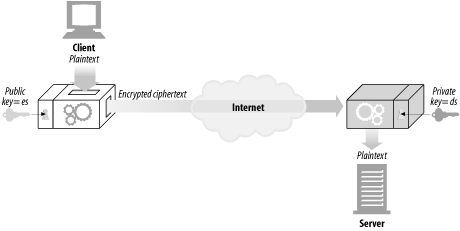
Figure 14-8. Public-key cryptography is asymmetric, using different keys for encoding and decoding
Node X can take its encoding key ex and publish it publicly.[7] Now anyone wanting to send a message to node X can use the same, well-known public key. Because each host is assigned an encoding key, which everyone uses, public-key cryptography avoids the N2 explosion of pairwise symmetric keys (see Figure 14-9).
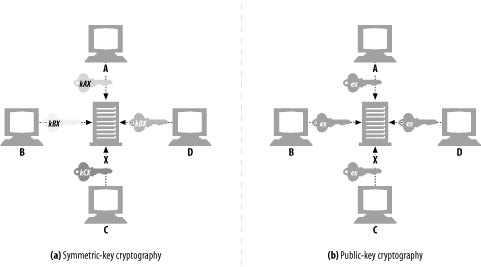
Figure 14-9. Public-key cryptography assigns a single, public encoding key to each host
Even though everyone can encode messages to X with the same key, no one other than X can decode the messages, because only X has the decoding private key dx. Splitting the keys lets anyone encode a message but restricts the ability ...