The easiest way to test the ATA functions is to simulate a DNS reconnaissance type attack, as follows:
- Log in to a domain computer.
- Open Command Prompt, type nslookup – REBELNET-PDC01.therebeladmin.com, and press Enter. The server name can be replaced by any domain controller fully qualified domain name (FQDN).
- Then type ls live.com.
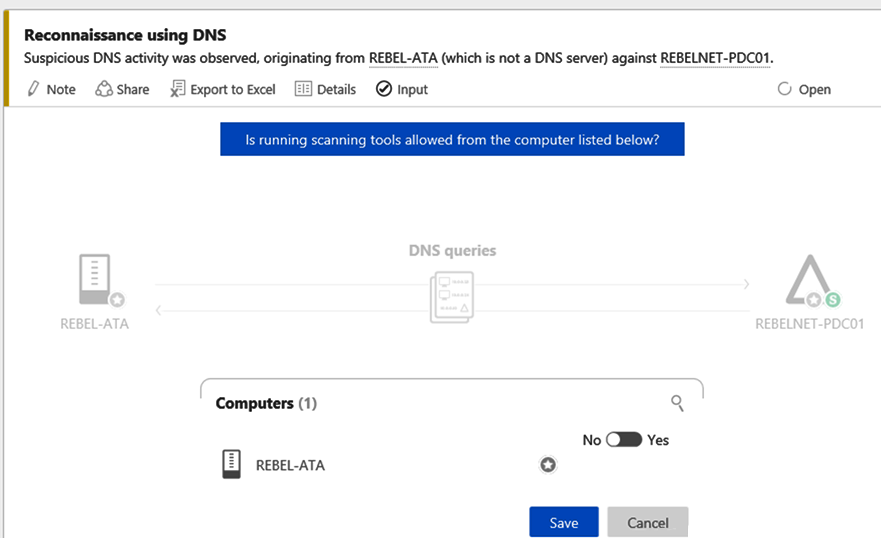
- Then log in to the ATA Center and check the timeline. There, we can see the detected event, as per the following screenshot:
- It provides a detailed explanation about the issue in a way that engineers can easily understand. These events also can be exported as a Microsoft Excel file.
- ATA also allows ...