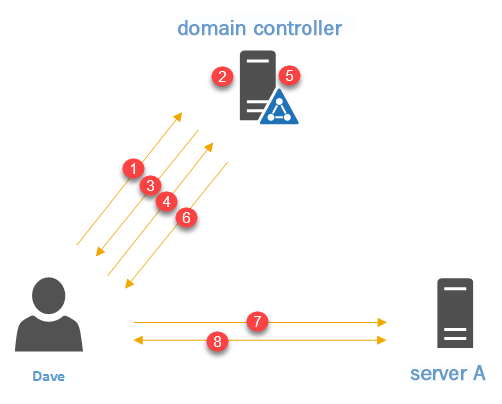
Let's go ahead and revisit our previous example, in order to see how authentication improves in an AD environment:
Following list summaries steps involved in the authentication process.
- Dave sends the username and his long-term key to the KDC (Domain Controller).
- The KDC checks the username and long-term key with its database and verifies the identity. Then, it generates a TGT. It includes a copy of a session key, which the KDC uses to communicate with Dave. This is encrypted using the KDC's long-term key. It also includes a copy of a session key that Dave can use to communicate with the KDC.
- The KDC responds ...