May 2020
Intermediate to advanced
262 pages
6h 48m
English
Vulnerabilities in our internet-facing interfaces may be exploited by cyber criminals. These vulnerabilities include using default passwords and out-of-date software updates. In the following diagram, we can see the vulnerabilities of the internet-facing interfaces of the smart doorbell application we built in the previous chapter:
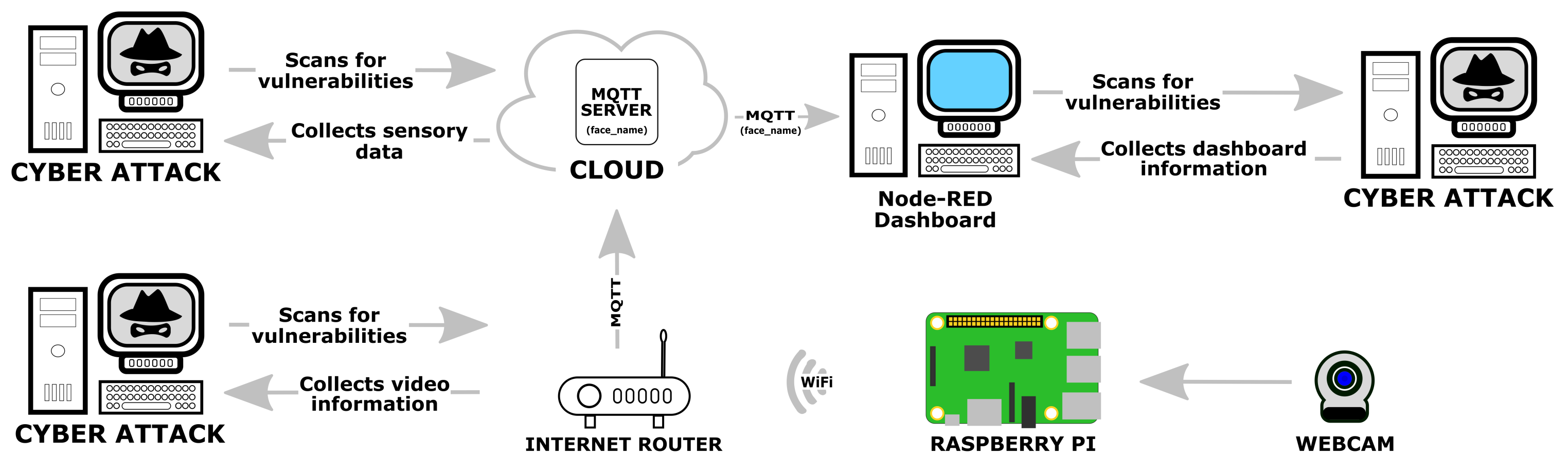
The biggest threat is an attack on an application's internet router. Through the internet router, a cyber criminal can gain access to a repository of photos of people that the application recognizes. This creates a privacy breach as this information could be used for nefarious reasons, possibly ...