September 2017
Intermediate to advanced
360 pages
9h 43m
English
We will now turn our attention to strategies for securing the backend components. The following diagram indicates the components we will consider, as shown in the shaded area:
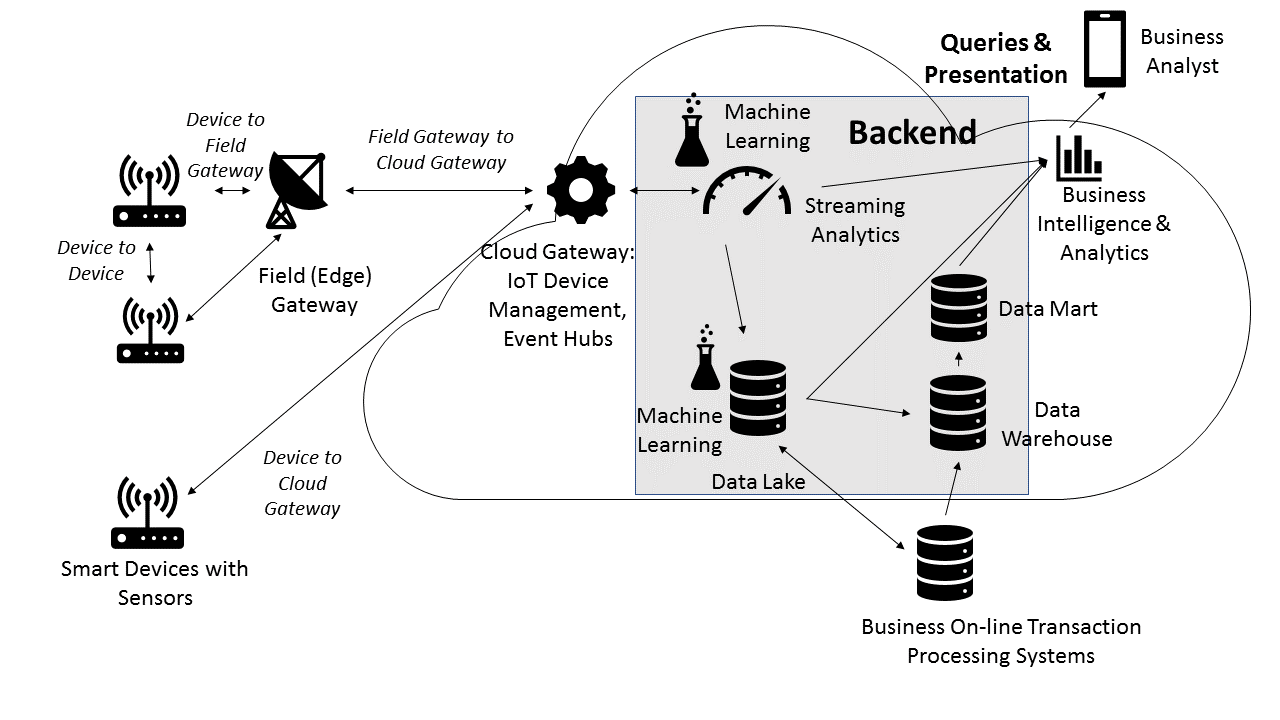
The streaming analytics engines provide a location to deploy applications, such as those that apply machine learning algorithms, on transient data. The security mechanisms for streaming analytics engines are less sophisticated today when compared to the data-management systems (such as the data lake, data warehouse, and data mart that are pictured). This is due, in part, to the limited requirements for administrative ...