September 2017
Intermediate to advanced
360 pages
9h 43m
English
Devices on the edge are typically located some distance from the backend data center and require unique physical, software-related, and data-security precautions. The data the devices gather is sometimes transmitted to other devices or is transmitted directly to cloud gateways or via field gateways onto the cloud.
In the following diagram, the shaded area indicates the components and networks that we will discuss securing in this section of the chapter:
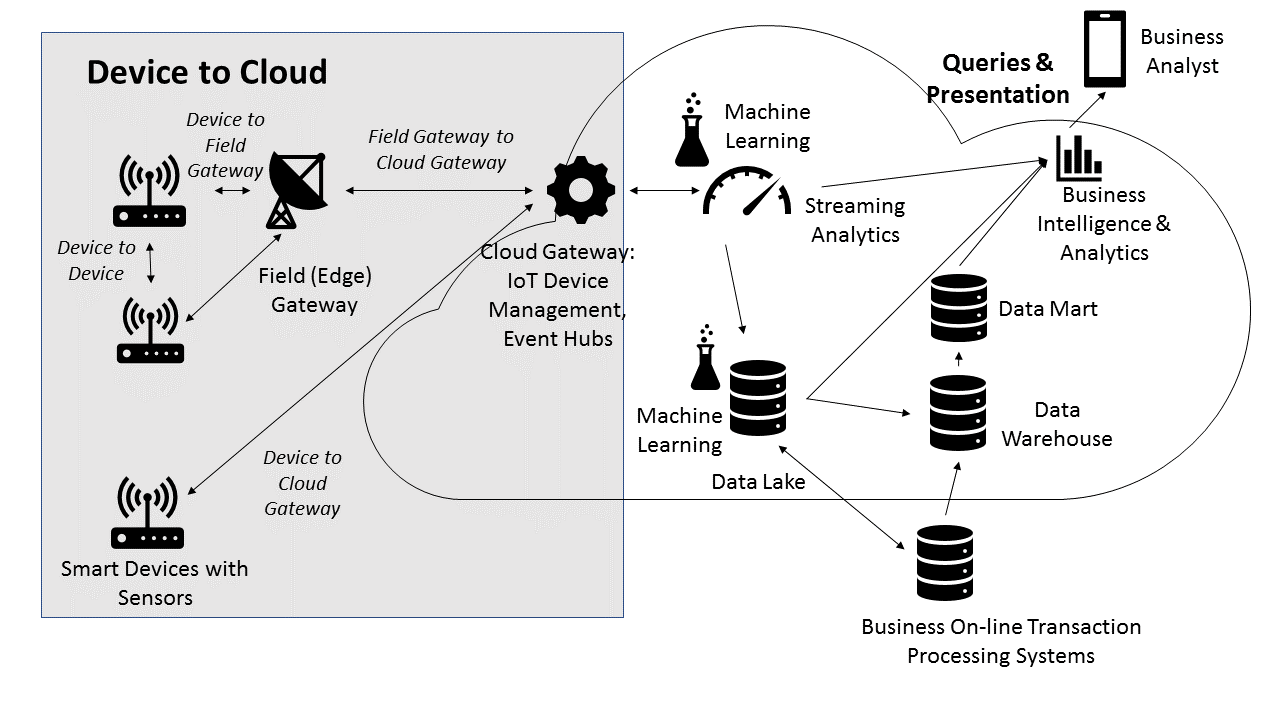
Connections and routes are established when peering occurs between the devices and the gateways. Secure ...