At the opposite end of the spectrum lie the apex predators of the social engineering world: the criminals who engage in highly targeted and, often enough, highly profitable campaigns of BEC. Unlike the scattershot approach taken by spammers in the previous example, the criminals who engage in BEC carefully target their victims, which may include looking for businesses that regularly send large sums of money overseas through wire transfer:
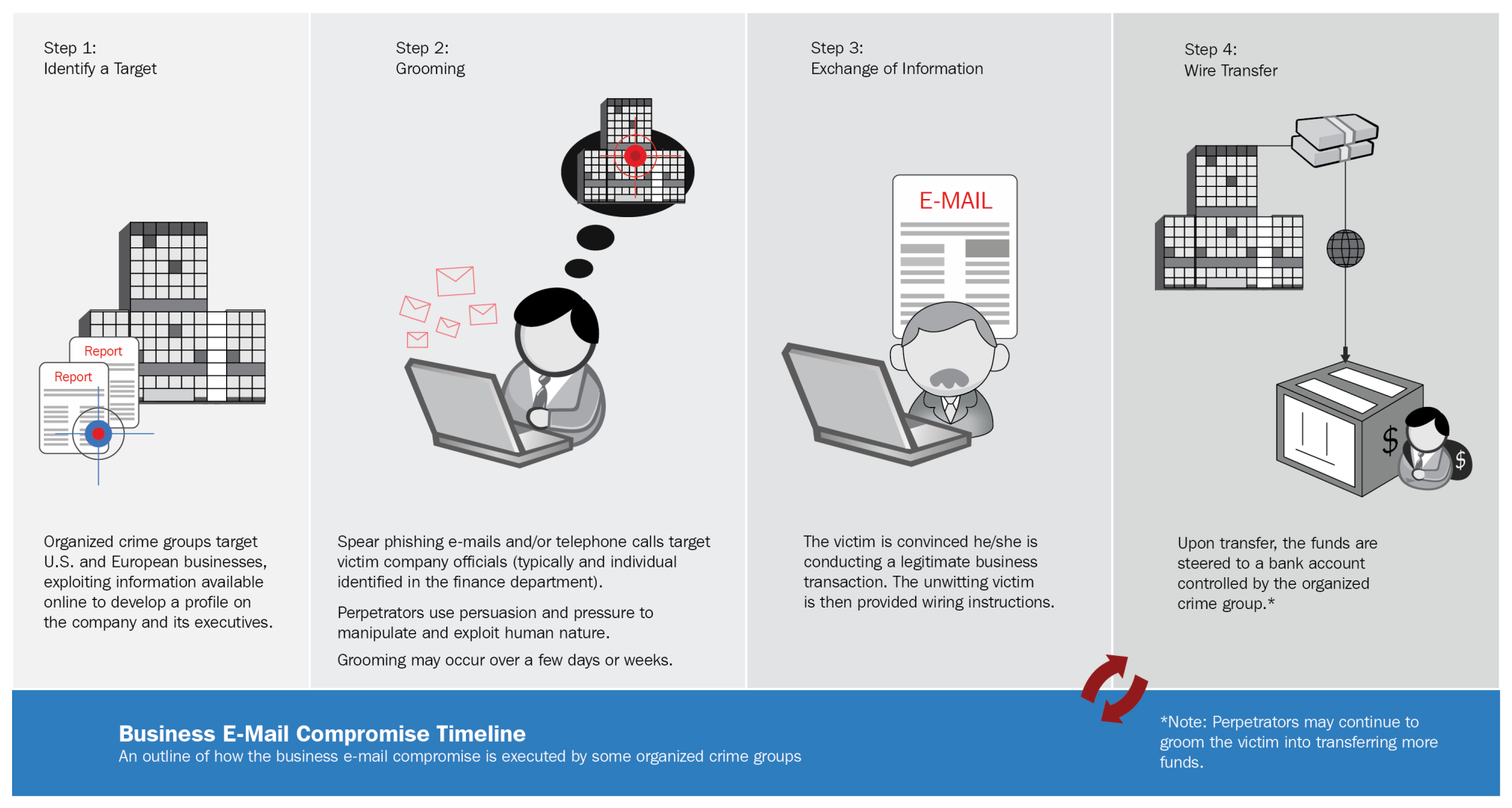
Just how large a problem is business email compromise for companies? A rather severe one, if the FBI's figures are accurate: ...

