As discussed, the data plane consists of the interfaces and the associated forwarding tables that are used for faster switching of packets. Any attack on the data plane would typically be an attack to push a lot of traffic through the network to try and block the legitimate traffic from being transported across the network.
The access network in an enterprise is typically a layer 2 network. The following figure shows the types of attacks that can happen at the access network at a layer 2 level and the defense mechanisms/features that are used to prevent these attacks:
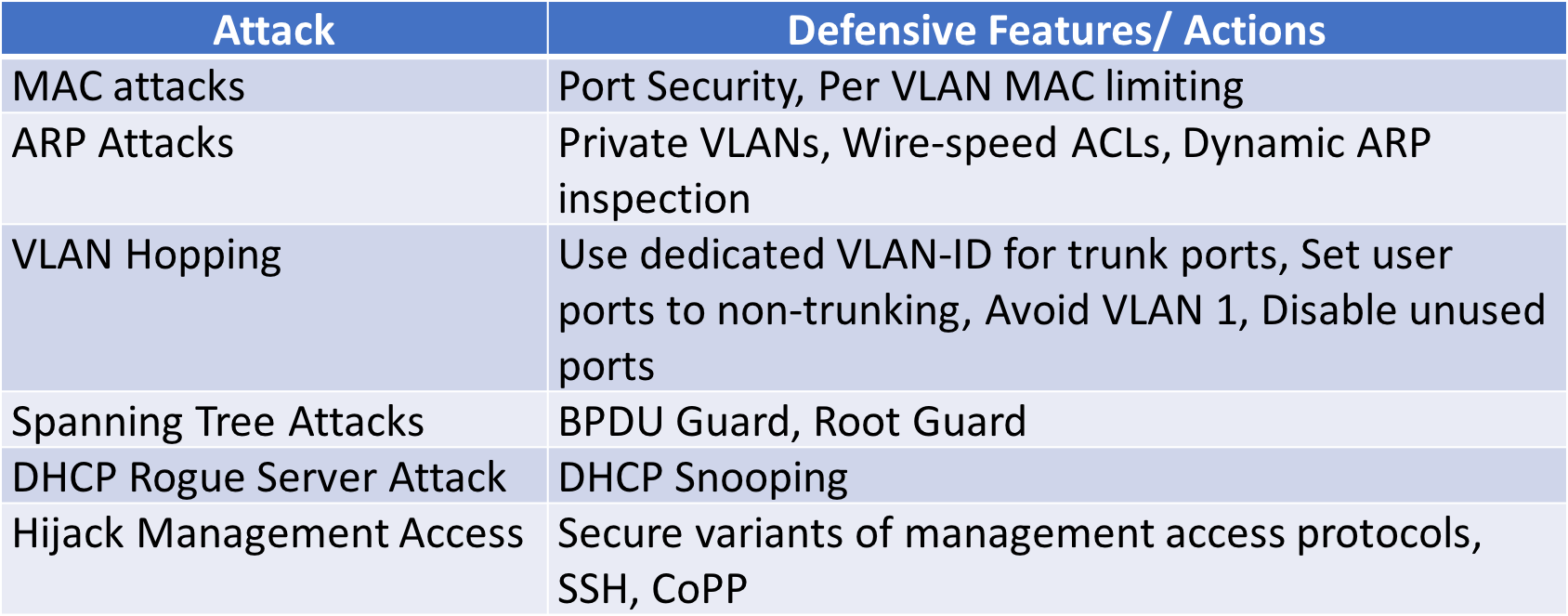
We will describe ...

